
Dual-WAN Enterprise Lab Project (In Progress)
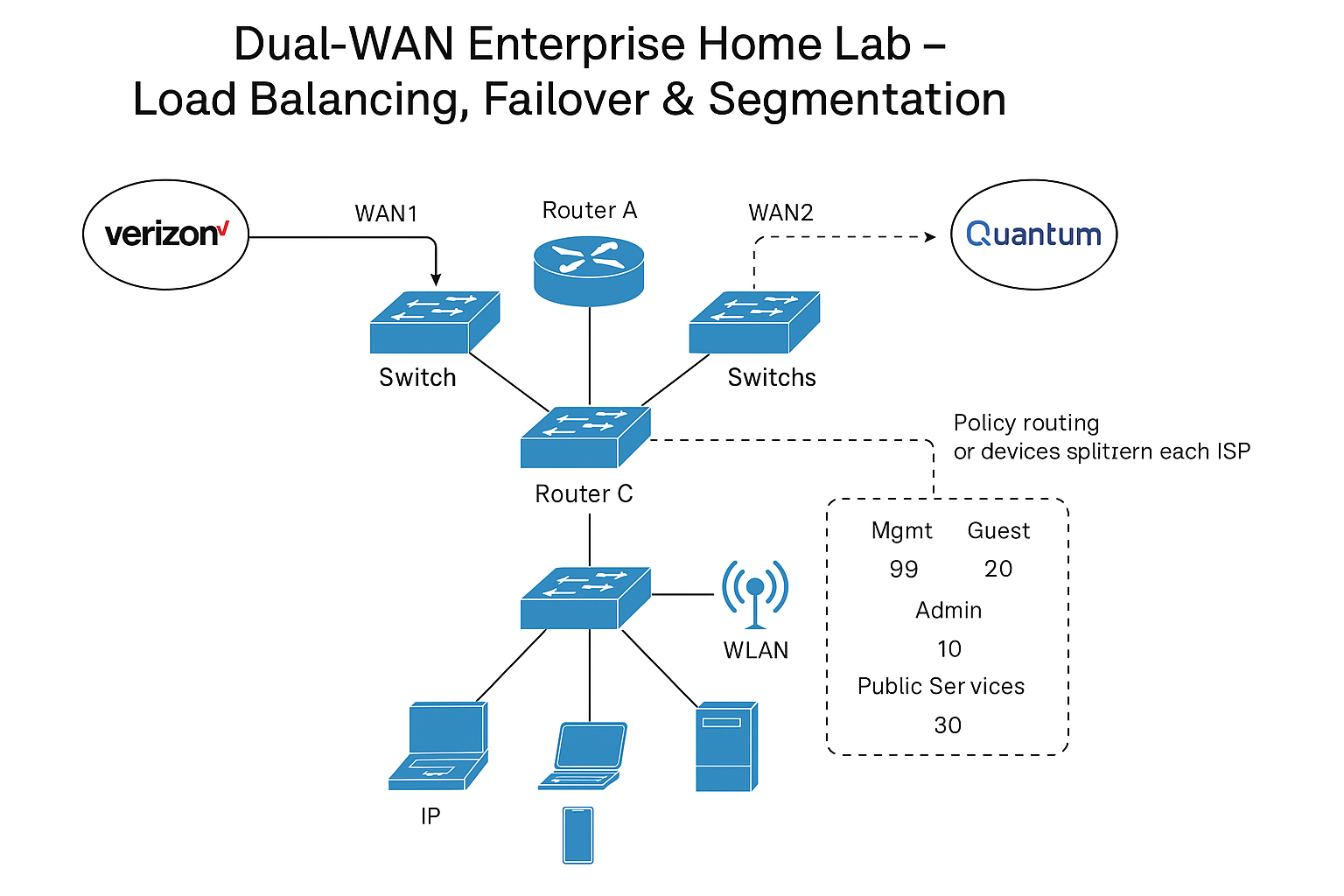
Lab Title: “Dual-WAN Enterprise Home Lab – Load Balancing, Failover & Segmentation”
Overview & Purpose
I’m currently building a professional-grade home networking lab that mirrors real-world enterprise network designs. This project is centered around a Dual-WAN (Multi-Homed) setup where I connect two different internet service providers — Verizon and Quantum Fiber — to simulate a multi-path, redundant internet environment.
The primary goal of this lab is to implement load balancing, failover mechanisms, and internal segmentation using VLANs and multiple routers and switches. This project gives me hands-on experience in everything from WAN redundancy to internal routing, security policies, and firewalling — all within a home lab environment.
Ultimately, this lab reflects my ability to build, manage, and document production-like infrastructure with real Cisco gear. Once complete, I’ll expand the lab into higher-level topics such as BGP, site-to-site VPNs, and cloud-edge integration, aligning with enterprise networking goals.
What I'm Building
-
Dual-WAN configuration with Verizon and Quantum Fiber
-
Three routers:
-
Verizon Gateway (Router A)
-
Quantum Gateway (Router B)
-
Core LAN Router (Router C, handling all routing/NAT/firewall logic)
-
-
Three switches to support:
-
VLAN trunking
-
Layer 3 routing
-
Port security and segmentation
-
-
Multiple VLANs:
-
VLAN 10 – Admin: My personal network, full access
-
VLAN 20 – Guest: Public Wi-Fi (with isolated traffic)
-
VLAN 30 – Services: Web server, SNMP, Syslog, etc.
-
(Optional) VLAN 40 – Lab/Testing
-
(Optional) VLAN 99 – Management for infrastructure control
-
-
Wi-Fi Access Point with VLAN-tagged SSIDs for Admin and Guest networks
-
Firewall rules and inter-VLAN access control
-
Policy-based routing: Split VLAN traffic between ISPs
-
Failover logic: If one ISP goes down, the other kicks in automatically
Technology Stack
-
Cisco 2821 Router – Core router for LAN side, NAT, inter-VLAN routing, PBR
-
Cisco IAD2400 Router – Connected to Verizon for WAN1
-
Cisco 1800 Series Router – Connected to Quantum for WAN2
-
Cisco Catalyst 3750 PoE-48 – Main Layer 3 switch, trunking + PoE for AP
-
Cisco Catalyst 3750 (24-port) – Inter-VLAN routing (backup or for services VLAN)
-
Cisco Catalyst 2960 – Layer 2 access switch for clients
-
Real CLI configuration with console access, static routing, OSPF, NAT, DHCP, and ACLs
How I’m Executing the Build
-
Planning & Topology Design – Finalized my VLAN/IP schema and drew out the logical network diagram.
-
Device Role Assignment – Strategically matched routers and switches to their optimal roles in the lab.
-
Step-by-Step Configuration:
-
Configured WAN links and verified internet access
-
Built internal VLANs and trunked ports across switches
-
Deployed NAT and DHCP per VLAN
-
Implemented static routing, with plans to transition to OSPF
-
-
Firewalling & Segmentation – Wrote custom ACLs to isolate guest and admin VLANs.
-
Documentation – Every step is being fully documented with screenshots, CLI configs, and network behavior explanations. I plan to host this documentation on my website as a showcase of my capabilities.
Why This Project Matters
This lab is far more than a hobby — it’s a serious, structured project aimed at sharpening my enterprise networking skills. I’m working with real Cisco equipment to solve real problems in a simulated enterprise environment. The concepts I'm implementing (failover, VLANs, routing protocols, firewalling, NAT, monitoring, etc.) are directly aligned with what businesses demand from network engineers today.
I'm treating this like a job. I dedicate time consistently to build it out, troubleshoot issues, and test scenarios. Everything I’m doing is tracked, written down, and designed to tell a story of what I know and what I can do.
Next Steps
Once this core lab is complete, my roadmap includes:
-
Introducing BGP between WAN routers for ISP control
-
Testing load balancing scenarios
-
Connecting to cloud services (AWS or Azure) over VPN
-
Creating automated failover scripts
-
Adding SNMP/NMS for monitoring
-
Building a case study or blog series from this project for career exposure